rm
Delete an object.
Usage
Flags
| Flag | Description |
|---|---|
--access string | the serialized access, or name of the access to use |
--encrypted | if true, treat paths as base64-encoded encrypted paths |
--help, -h | help for rm |
--parallelism, -p int | Controls how many removes to perform in parallel (default 1) |
--pending | Remove pending object uploads instead |
--recursive, -r | Remove recursively |
--help, -h | help for rm |
Examples
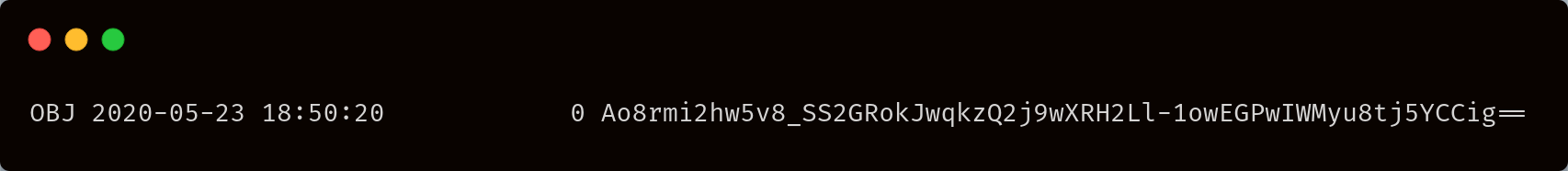
Delete an object
Delete an encrypted object
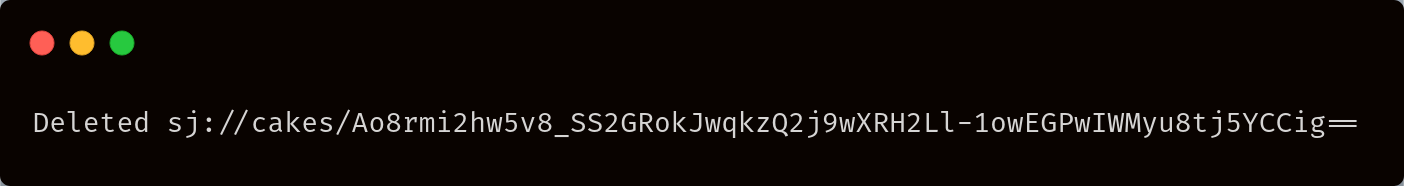
If an object has been created with another encryption key, you won't be able to read it, but you can delete it. In order to delete an encrypted object, you have to know its encrypted path. To retrieve it, you can use the list command ls with the encrypted file. For instance, to list the encrypted path of the objects in a bucket sj://cakes you could use:
You can then use this path to delete the encrypted object: